LILCTF2025
应该是最后一场比赛了,拼尽全力无法战胜
Crypto
ez_math
1 | |
恶补了下线代,都忘光了
因此C和是相似矩阵,特征值相同,为和
求解特征多项式
用sage很快就出来了
1 | |
mid_math
1 | |
把上一题喂给deepseek-r1就可以了
问题分析
该问题结合了线性代数和AES加密,需要从给定的矩阵和密文中恢复加密密钥。以下是关键点分析:
1. 矩阵结构分析
- 矩阵 由5个随机64位素数向量组成:
- 矩阵 是标量乘法结果:,其中
- 矩阵
- 矩阵
2. 关键数学关系
- ,因此 的特征值为
- ,特征值为
- 核心洞察: 和 的特征值存在指数关系:
- 非零特征值满足
- 特征值直接对应
3. 加密流程
- 生成随机密钥
- 使用 PKCS#7 填充将 扩展为 16 字节 AES 密钥
- 用 AES-ECB 加密填充后的 flag(填充至 64 字节)
- 输出 和密文
4. 攻击思路
- 提取特征值:
- 计算 的特征值
- 计算 的特征值
- 求解密钥:
- 对每对非零特征值 求解离散对数
- 验证 是否满足所有特征值关系
- 解密 flag:
- 用 重构 AES 密钥
- AES-ECB 解密并去除填充
解决方案代码
python
1 | |
Linear
1 | |
类似于背包,参考ezbag:HGAME2025-Crypto - Naby的博客
就多乘一个数,尽量得到最小向量
1 | |
baaaaaag
1 | |
参考ezbag:HGAME2025-Crypto - Naby的博客
就多了个block_size
1 | |
Misc
是谁没有阅读参赛须知?
LILCTF{Me4n1ngFu1_w0rDs}
Web
ez_bottle
稍微看了下bottle,发现这过滤的基本没过滤,让AI快速搓个交互脚本后,发现卡在怎么回显
最后在这里发现了可以触发报错
https://blog.csdn.net/weixin_59166557/article/details/146161897
1 | |
*Ekko_note
只做到了解决uuid8的部分,后面不会了
通过尝试搜索低版本python的uuid8,刚好发现拉面特徐师傅的博客
得到uuid8生成代码:
1 | |
a可知是admin\x00
随机数种子是固定的
登陆后可以在/server_info 查看到服务器启动时间 random.seed(SERVER_START_TIME)
_RFC_4122_VERSION_8_FLAGS的值根据RFC标准RFC 9562: Universally Unique IDentifiers (UUIDs)
1 | |
M和N的最高位都为1,换算一下就出来了
然后就可以修改admin账号的密码了
后面就不会了
Reverse
ARM ASM
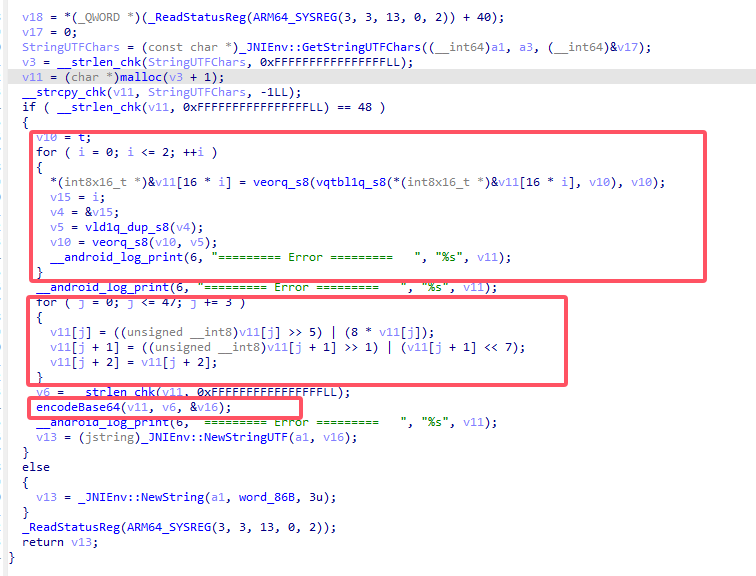
有三个看不懂的函数veorq_s8, vqtbl1q_s8, vld1q_dup_s8
通过搜索得知这是neon指令集,简单说就是:
veorq_s8: 异或
vqtbl1q_s8: 取对应索引位置的值
vld1q_dup_s8: 将一个值扩展到(一个寄存器的)所有通道(?) 这里理解就是一个数组
知道这些就很简单了
比较坑的就是这base64的表不是常规表,用cyberChef换一下就好了
1 | |